ThreatSTOP
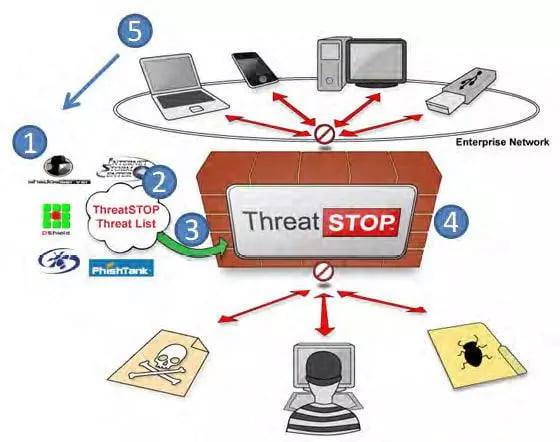
ThreatSTOP’s 5 Parts:
- Multiple threat feeds
- Correlation engine
- Firewall configuration and DNS distribution
- Blocking malware
- Reporting and feedback loop
The Five Parts to ThreatSTOP’s Service
ThreatSTOP is a real-time threat intelligence service that automatically delivers a block list against criminal malware (botnets, Trojans, worms etc.) directly to your firewalls, so they can enforce it. It is a cloud-based service that protects your network against the most serious information security problem today—malware designed to steal your most valuable data perpetrated by organized criminals. ThreatSTOP enables your existing firewalls and network infrastructure to enforce your malware blocking policy without requiring the expense, complexity and time of a forklift upgrade of new equipment. It can be deployed within the hour with simple rule-settings or a script on your firewall.
1. Threat Feeds
We aggregate threat feeds from leading malware monitors and our own feeds from honeynets, law enforcement and other proprietary sources. Due to our deep relationship with many leading monitors, such as DShield and several others, we also receive private feeds not available to the public. We currently aggregate from more than 45 sources. The following is a sample of our feed sources:
- DShield
- SpamHaus
- Shadowserver
- AutoShun
- PhishTank
- Abuse.ch
- Emerging
- Threats
ThreatSTOP maintains one of the most comprehensive and authoritative threat lists in the market today due to its feed sources and the longevity of its database. We currently track over 25 million IP addresses, and are constantly culling and monitoring current and new sources to improve coverage and accuracy. We have a 5-year history on most of these addresses. From some feeds, such as DShield, we have their entire history since 2001 when Code Red hit, which is to say, the beginning of time (as far as modern malware goes). Finally, we get large volumes of daily feeds from our customers’ logs of live traffic and attack data that go back into our threat
database.
2. Correlation Engine
Our correlation engine filters the raw feeds to produce a predictive threat list by evaluating factors such as:
- Dates an IP address is first and last seen in our database
- Frequency of appearance
- How many sources have reported it
Our algorithms are weighted for low false-positives. An address that appears in multiple reports from different sources is more likely to be added than one from the same source multiple times. Likewise, an address which has been on our list before is more likely to be added than one that has never been seen before. Finally we check to make sure that the address is not on our global whitelist of major Internet sites and we will remove it if it is. This is done because cyber criminals frequently seek to poison IP reputation services by spoofing the address of someone else and because the major sites are very active in first removing malware on their servers and then taking over the domains used by bot herders.
IP addresses, or rather the computers they represent, are also continually getting fixed and so an IP Reputation service must promptly remove addresses that are now no longer a problem.
Our algorithms are careful to ensure that our feeds do actively prune addresses that are no longer active. We also use the logs of our subscribers to validate and confirm whether an IP address should be removed or not.
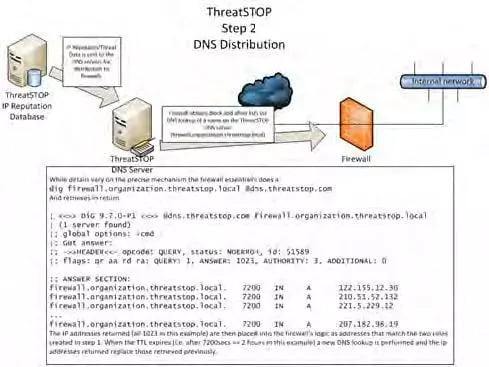
The resultant threat list is currently about 30,000 entries (22,000 IP addresses plus 8,000 /24 subnets), and updated every 15 minutes. The ThreatSTOP Threat List is used, in conjunction with user selected criteria, to generate the DNS lookups posted on our DNS servers so our customers’ firewalls can retrieve them as their block rules.:
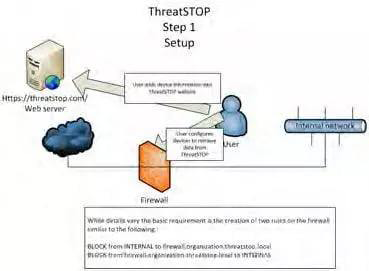
3. Firewall configuration and DNS distribution
This is the key that makes ThreatSTOP unique and actionable for the mainstream market by enabling the automatic distribution of the ThreatSTOP Threat List to a supported firewall through a DNS lookup. Once set up, which typically takes about an hour or so, your network is protected by ThreatSTOP. The first step is to register the firewall’s IP address with ThreatSTOP and select what you are trying to protect, so we can determine what block lists it should use. The second step is to apply the new rules to the firewall. For some firewalls, such as Vyatta, ThreatSTOP supplies a configuration script that is downloaded and run by pasting a line into an SSH terminal session. For others the rules are added manually, and the rules are typically:
DROP and LOG FROM TO firewall.organization.threatstop.local
DROP and LOG FROM firewall.organization.threatstop.local TO
If no setup script is available for that particular firewall, the subscriber also needs to follow the instructions provided by ThreatSTOP to set up DNS resolution of threatstop.local and log upload for firewalls. We are constantly adding setup scripts and log upload automation, which is what we mean by saying a firewall is “supported”
Once the firewall setup has been committed it looks up the name configured in the setup phase and the ThreatSTOP DNS server returns the Threat List configured for that firewall. The firewall will get the list during its regular updates with the DNS server, which can be set by the administrator, or rely on the DNS Time To Live that ThreatSTOP configures and which ThreatSTOP can vary as the rate of change of data varies.
4. Block malware
Once the current threat list is retrieved, it is placed in the firewall’s memory and every packet passing through is checked against it. There is no performance impact for a new connection because, unlike an RBL, the DNS lookup occurs before packets are received. The default mode is to block all traffic to and from IP addresses on our threat list. There are, however, other deployment options:
- Log-only mode—just observe, do not block
- Redirect—for deeper inspection, tar pitting, or analysis
- Customize white/black lists—modify our list with your own changes
- Expert mode—use our list a la carte, and pick specific feeds for your needs
5. Reporting and feedback loop
Web-based reports that enable remediation of infected internal hosts and facilitate compliance are included in the ThreatSTOP service. By highlighting connections to and from known bad actors, the ThreatSTOP reports cut through the noise and give you information you can use to better secure your network, without sifting through verbose text-based and illegible firewall logs. These reports can be integrated with your SEIM or converted into a simple Excel file to manually perform remediation and forensics on breached machines. We currently provide three levels of reports:
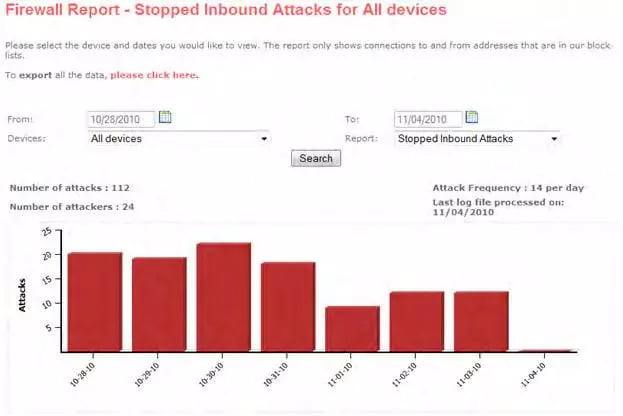
1. Overall Blocking Stats
This reports totals the number of inbound and outbound attacks blocked by ThreatSTOP for a given time period.
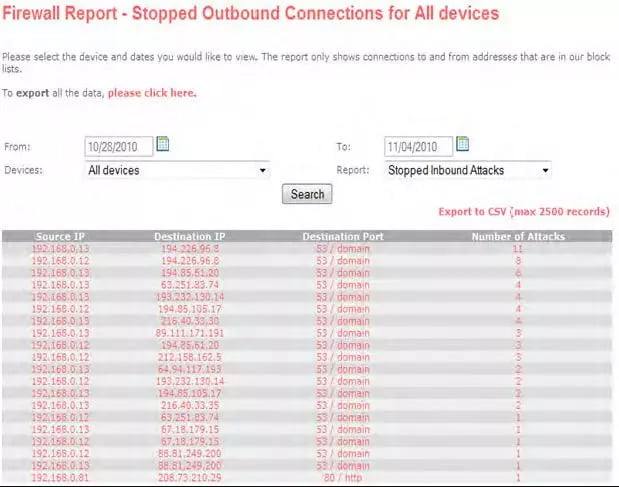
2. Summary of blocked addresses
This report drills down on the blocks a bit further to include source/destination IP address, destination port and the number of attacks.
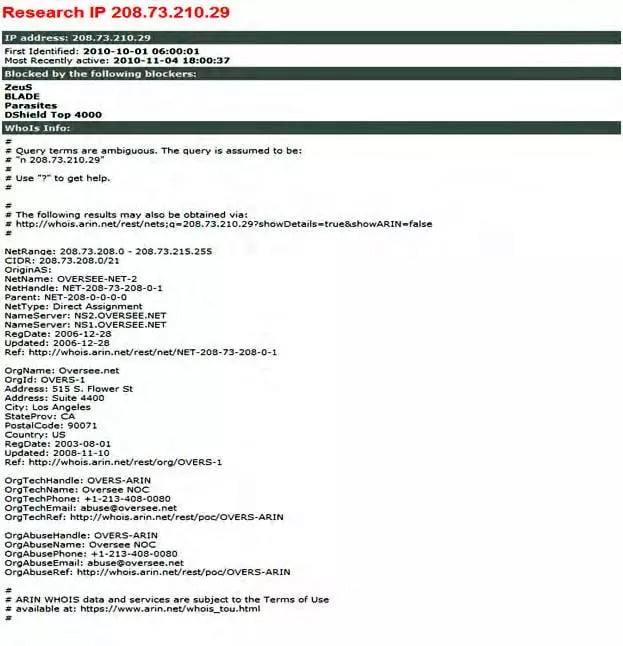
3. Individual address analysis
This report profiles a specific IP address in question, akin to a rap sheet. It is very useful for forensics and prosecution. It details:
- First identified
- Most recent activity
- Reporting sources
- Provenance of the address (WhoIS-type info)
As a result of users submitting logs to generate these reports, ThreatSTOP provides a feedback loop for the system by integrating
logs of real-world traffic and attack events into our threat feeds to improve coverage and accuracy of our list. The result is that each additional user increases the breadth and accuracy of the ThreatSTOP Threat List, reduces the time to detect new malicious hosts, and enables ThreatSTOP to provide a collaborative network defense for all members of its network.